Introduction – welcome and what to know? (optional) (helpful for beginners)
Hi Web3 noobs (from a fellow Web3 noob). Before you embark on this read, there are a few things that you should understand at a high level in order to make the most of the resources included in this pamphlet. Here are some links to understand basic blockchain concepts and common terms that you may stumble across as you read this:
What even is a blockchain?
Simple guide to understanding blockchain
Evolution of web3, explained Web3, plus the history of web1 and web2!
What’s so different about DeFi? What’s CeFi? Comparing CeFi and DeFi, with high level explanations of both
Ok…now what’s a CEX…what’s a DEX? Comparing CEXs and DEXs
Governance basics Proof of stake vs proof of work
What’s wrong with blockchain tech? → what do most of these topics seek to address in the space?
Major challenges with blockchain
Blockchain scalability – what is it and what’s the issue?
Deep dive into blockchain scalability
Blockchain interoperability – what’s going on between chains?
Beginner’s guide to interoperability
Intro to blockchain proofs
Blockchain consensus mechanisms overview
ZK and Potential Applications
Intuitive example of a zero knowledge proof. (Source: Chainlink)
Executive Summary
A zero knowledge proof (ZKP) is an encryption method that enables one party to prove to another party that a certain statement is true, without revealing any information beyond the truth of the statement, such as having any insight into the information itself
First proposed as a interactive proof system, where a Prover exchanges with a Verifier to convince the Verifier that some mathematical statement is true
However, what happens when the verifier also cannot be trusted?
ZKPs introduce a solution in which the Prover can prove a fact to the Verifier without the Verifier knowing the thing that the Prover is trying to prove.
Allows private information to be kept secret in an exchange while upholding security and verifiability
Emerged as an important technology for the privacy and security of blockchain systems, with potential to be used in scaling ventures
ZKPs are particularly useful for ensuring the integrity of decentralized systems, where trust must be established among parties yet information is sensitive
Must fulfill three conditions – completeness, soundness, and zero-knowledge
Tech, Explained
When first proposed, ZKPs relied on a series of multiple interactions to prove a truth – this would be an interactive proof
Now, things can be proven and verified within a single interaction, which makes the whole process more efficient and eliminates the need for a series of interactions. This reduction of time and energy makes it possible for zero-knowledge proofs to be deployed at scale – this is a non interactive proof
Non interactive ZKPs do not need beyond a single interaction between the prover and verifier; the prover would present proof of knowledge and the verifier would confirm its genuineness within one exchange
Since they only require one information exchange, they demand more computing power
This shared cryptographic key between the prover and the verifier works similarly to a private or public key that is commonly seen in blockchain wallets
Most current use cases of ZKPs in blockchain technologies include:
zk-SNARKs: zk-SNARKs (Zero-Knowledge Succinct Non-Interactive Argument of Knowledge) is a type of ZKP that is widely used to make cryptocurrency payments more private and build zero-knowledge protocols.
Since these are non-interactive, the proof size is small and paves the way for easy and efficient verifications
Everything from proof generation to submission to verification happens within a single transaction
Require a trusted setup between prover and verifier – this typically looks like a set of public parameters along with the creation of cryptographic keys
With limited computation power, the system cannot be cheated, which adds the quality of computational soundness to SNARKs
The requirement of a trusted setup phase to generate randomness is a potential point of security concern
Not quantum resistant
Smaller byte size compared to STARKs, but computational demand makes it such that they are slower in proof generation. However, they consume less gas and are generally more efficient
Used by privacy coins such as Zcash (see projects below)
zk-STARKs: zk-STARKs (Zero-Knowledge Scalable Transparent Knowledge of Argument) are now widely deployed in Layer 2 scaling platforms. These are a slightly newer model, first published in 2018, so these are generally less widespread than the SNARK protocol.
These proofs focus on enhancing scalability, allowing developers to perform computations and store data off-chain, which significantly increases scalability
Used to verify these off-chain activities and are subsequently shared online for interested parties to confirm their validity
The implementation of transparency in STARKs largely differentiate them from SNARKs, meaning that they use publicly-available randomness to generate parameters, hence eliminating the need for a trust setup
Uses hash functions, a storage saving tool, which are more resistant to collisions as part of their argument of knowledge computation
More quantum resistant
Since the parameters are public, this limits centralization and empowers transparency
Another interesting use case would be in Merkle Trees, which are data structures that enable efficient verification of large amounts of data by only requiring a small amount of information to be transmitted
Applications
As blockchain technology becomes bigger in terms of usability and productivity, scalability has become a huge challenge
Network congestion results in increased transaction fees, which makes it difficult for Web3 to become massly adopted
ZK-rollups are Layer-2 scaling solutions that help to increase throughput and efficiency on mainnets, all while being more energy efficient.
These rollups complete computations and state storage off-chain, helping Layer-1 blockchains process more transactions and incur less fees while doing so
Since rollups typically process thousands of transactions at once, each one requiring proof of transaction for on-chain actions, ZK-rollups process these batches more efficiently by posting only the minimum summary of data on-chain transactions
More on ZK-Rollups later!
Most use either SNARKs or STARKs
ZKPs also power several privacy protocols, due to their ability to be non-disclosure
Allows users to transact on privacy-enabled blockchains and post ZK proofs that will confirm that their transactions are valid without revealing any details of the transaction
ZKPs as a part of bridging protocols can be designed to increase the characteristics of trustlessness and decentralizing in cross-chain bridge models
The accuracy of transaction details on source blockchains are typically proven by SNARKs, with little to no reliance on external trusted parties – as long as the connected blockchains and the network are deemed secure, and there is at least one honest node in the chain from which the source comes from, the bridge is secure
Makes bridges more permissionless and decentralized, as ZKPs will sever the reliance that bridges typically have on commonly-used centralized methods of validation and verification, such as the Proof-of-Stake style network validation models
Allows for new features to be added easily and for protocols to connect with the bridge
Becomes powerful tool for blockchain interoperability
zkEVMs
Zero-knowledge rollups that aim to bring ETH fully to layer-2 blockchains
Goal is to retain all the current usability of rollups
Important applicability in identity as well, as ZK will allow for identifications to be proving online without revealing the details of the identity
Authentication scheme where one party will prove to the other that they hold knowledge that would prove ownership of the identity
Does not require complicated methods of encryption, and improves user experience and upholds user privacy by keeping important information anonymous
Improving the ways that identity authentication happens on blockchains also improves scalability
Key Projects
Starkware, Zcash
Zcash uses SNARK cryptography to restore blockchain anonymity for their users and give their control over their transaction information
When one user sends coins to another user, the only available proof of their privacy-enabled transaction comes with ZK – for instance, a third-party would be unable to find any additional secret information about the transaction, the parties, and the amount involved
Starkware utilizes STARKs to promise scalability in StarkNet, operating as a L2 network over ETH
Aims to help any decentralized application to achieve unlimited scale for its computation
Permissionless decentralized validity-rollup – more on this later in ZK Rollups
zkSYNC is a L2 zkEVM solution for transaction Ether and ERC20 tokens, positioned as a scaling and privacy engine for ETH using SNARKs
Promises low gas usage and efficiency while having no compromise on security
Helps to offload ETH’s network traffic by bringing some transactions off-chain
Read More
ZK Rollups: Making Scalable Blockchains Possible
Private Transactions on Ethereum Now
More on zk-SNARKs and their setup
zkSNARKs explained by Quantstamp
Bridges
Executive Summary
All blockchains have their limitations – for example, blockchains encountering scalability issues have integrated L2 rollups, and L1s are designed in a different way that allows greater throughput efficiency yet acts as a barrier to decentralization.
Since these blockchains are all isolated in development, and have different governing principles, there is no native level of communication and tokens are stuck on the chain on which they are created or initiated.
Bridges are protocols that allow the transfer of assets or data between two different blockchain networks and connect blockchain ecosystems.
Bridges enable:
Cross-chain transfer of coins, assets, and information
Users to access new platforms while leveraging the benefits of different platforms (e.g. bridging assets to play a game on a fast chain and back to a slower, secure chain to trade assets)
Developers from different ecosystems to collaborate
Some bridge use cases include:
Lower transaction costs, as users can bridge their assets to different platforms with lower transaction fees
Dapps on other blockchain platforms, as users can move onto different chains to lend and buy
Owning native crypto assets by bridging funds from different chains
All of these are doable on centralized exchanges, but bridges provide a much more efficient way
Bridges enable interoperability between different networks, which is essential for later scalability and further development of the whole ecosystem
Bridges require robust security measures and audits
Tech, Explained
Previously, if a user held assets on one chain but wanted to invest on another, the most direct way was to swap them through a centralized exchange. This was expensive 🙁
Development of cross-chain tech allows users to interoperate between different blockchains
Most current solutions of bridges are based on the central authority: bridges have an account on the source chain where users deposit their tokens, and in response, a central authority (software program) will signal a smart contract on the target chain to begin
Problem: there needs to be a way to lock the assets on the original chain before minting or releasing an equivalent asset on the target chain
Solution: smart contracts!
Users send their tokens to a smart contract, which gains custody of the user assets
Protocol will communicate this to another smart contract on the destination chain
Releases the equivalent amount of funds
In this sense, bridges are a misnomer: assets are not genuinely moved from chain to chain, but rather locked up on one chain and releasing an equivalent asset on the second chain
Sometimes, bridges will burn the asset on the original chain, minting it on the second – avoids the issue of maintaining 1:1 backing, increases gas fees and makes the process more complex though
Bridges are one way or two way
If they are one way, assets can only be sent in one direction
Wrapped Bitcoin → can be used to send BTC to the ETH blockchain
Many adopt the lock, mint, and burn model in the design, which summaries the techniques described above
Users lock funds on the original chain → bridge verifies that their fund is locked → mint wrapped tokens on destination chain
Decentralized, trustless bridges don’t require centralized intermediaries and instead rely on decentralized machine algorithms (smart contracts) to operate
Individual networks contribute to transaction validation
Give significant security and more flexibility, but less efficient
Different protocols will take different approaches to how validators are incentivized and how information accuracy is ensured – ie. whether the relay network is permissionless and how relayers achieve consensus
Some bridges will have fully trustless relayers, which create on-chain light clients that verify relayed information and call the functions to mind, burn, and unlock accordingly
Centralized, trusted bridges
Also known as federation or custodial bridges
When moving large amounts of currency, trust bridges are rapid and somewhat cost effective
Leave room for security risk as there is no incentive for federation members to receive reward for detecting and preventing fraud during transactions
Would have a group of whitelisted relayers, which would together control the minting and burning of wrapped tokens via multisig.
Validators are typically subject to KYC, and thus mutually trusted
Other bridges are built on a Proof of Stake network that allows anyone to be a validator, which can be existing ones or new ones formed specifically for the purpose of cross-chain communication
Unique advantages:
Transaction between chains, little network activity, improved development experience, decreasing monopolization amongst chains
Issues to address:
How can we address liquidity fragmentation across bridges when different bridges have different wrapped tokens?
How do we design a secure bridge?
Lots of security issues happen during this bridge exchange
Smart contract risks
Technology risks
Censorship risks
Custodial risks
At a high level, bridges will always be inherently insecure in their design and the ecosystem will eventually need to innovate away from the concept
Applications
Interoperability of blockchain focuses on solving three main issues:
Interoperability of the application layer
Tight coupling between the upper layer application and the underlying chain
Interoperability between chains
“Chain-level silos”
Ability to leverage the functionalities of different chains on others to take the most advantage of the benefits of different protocols
Interoperability of data off the chain
Solves the secure and trustworthy interaction of data that is not on-chain
Dapps to access the strengths of various blockchains
Enhances capabilities and makes it such that protocols have more room for innovation
Users to access new platforms and leverage benefits of different chains
Developers from different blockchain ecosystems to collaborate, improving the development process and experience for on-chain builders!
Also incur lower transaction fees in relation to using third parties to move assets from chain to chain
Key Projects
Wormhole – supports 20+ builders for developers, bridges tokens across all over the ecosystem
Connext Bridge – supports variable L1 and L2 platforms, and different stablecoins. Uses noncustodial Xdomain transfer protocol to enable generalized cross chain transfers
Multichain – supports array of blockchains and assets and benefits from large maximum bridge amounts; known as a more feature-complete bridge?
Celer cBridge – features user contributed liquidity and support for many blockchains and assets – supports Celo and Aurora platforms!
Allbridge – simple routing platform that is designed to keep fees to a minimum
Portal – built to bridge Solana assets to and from other chains, allows users to swap Wormhole wrapped tokens with low fees, supports different blockchains and supports NFT transfers unlike others!
Polkadot – wants to allow heterogeneous and economically independent blockchains to communicate with one another. Working on UI in interoperability specifically with their designs
Read More
EvoDefi's Cross-Chain Bridge Deep Dive
Scaling
Executive Summary
Scaling is a bottleneck of the cryptocurrency world. It’s not possible to onboard the world right now onto crypto as a financial system, due to transaction times and capacity limitations
Scalability trilemma: can only achieve two out of three of decentralization, scalability, or security
Decentralization is typically the property that makes blockchains slow, since the network can only operate at the speed of the slowest node
Scalability determines the network’s capacity, including the number of nodes in the network, the number of transactions that the network can process, how fast the network can process, etc
Blockchains have historically struggled to maintain trust minimization for use cases that require speeds and costs comparable to traditional computing systems
Trust minimization generally refers to the principle of seeking to optimize predictability in protocols by accounting for all factors
Felt by users in the form of high transactions costs
Create doubt around whether blockchains can support high value transactions that hinge on handling data in real time
The trust models of traditional computing environments do not prioritize trust minimization so greatly, which is why they are able to lower costs and raise efficiency easily
Concepts Explained
Key properties of blockchain scaling:
Execution – computation required to execute transactions and perform state changes, involves checking the validity of transactions using cryptography and executing the on-chain logic needed to calculate changes
In terms of scalability, the issue is increasing throughput. Want to achieve more computations per second without substantially increasing the hardware requirements
Storage – storage requirements of full nodes whom need to maintain and store a copy of the ledger through historical data and global states
As ledger and associated storage grow in terms of size requirements, the computation of state becomes slower and more expensive because nodes require more time and computations to read from and write to state
When scaling the storage layer, the main problem is to solve how blockchains can process and validate more data without increasing storage requirements for full nodes
Blockchain consensus – when scaling, want to reach finality faster and more efficiently in terms of both cost and trust minimization
Second layer (L2) scalability solutions or off-chain solutions add a second layer to the main blockchain network to facilitate faster transactions, building upon the main blockchain to off-load transactions to reduce the amount of space and network congestion
Sidechains – used to offload from the mainchain by moving certain applications onto the sidechain, which is simply a separate blockchain linked to the main one.
Applications
Most L2 scaling solutions are centered around a server/cluster of servers that are nodes with the ability to be run by the entities that use them – instead of transactions being submitted to the mainnet, transactions are submitted to these layer 2 nodes instead
This is quicker and cheaper because the layer 2 nodes can process transactions off-chain, without having to wait for the slower and more expensive on-chain processing that happens on the Ethereum mainnet. The layer 2 nodes can perform a variety of optimizations that are not possible on the mainnet, such as batch processing multiple transactions together, aggregating transactions from multiple users, and compressing data to reduce the amount of data that needs to be processed
Layer 2 is needed to increase transactions per second (improves UX and network performance), reduce gas fees on mainnet by rolling up transactions, reduce the burden of scalability on decentralization and security, etc
Makes it more accessible for developers to build decentralized applications
Key Projects
Polygon (Ethereum) – Works by handling Eth’s transactions on a separate sidechain, then returning transactions post-processing, which lowers the network load on Eth and reduces the transaction and time costs
Using Polygon, users can interact with any DApp without worrying about network congestion
Lightning Network (Bitcoin) – leverages the concept of payment channels and enables the creation of a peer-to-peer payment channel between two parties. After establishing this connection, the channel allows the parties to send an unlimited amount of transactions that are instant and pretty cheap
Subject to many transactional risks, as when funds are locked into the payment channels, they have a lot of counterparty risk and functional instability
Polkadot – uses and popularized parachains, which run parallel to the Relay China and are able to parallelize multiple transactions to help achieve desired scalability
Read More
High level overview of L2 scaling solutions
Polkadot – sharding and parachains
Rollups – Optimistic Rollups
Executive Summary
Layer 2 protocols designed to extend the throughput of the base layer
Reduce computation on the main chain by processing transactions off-chain, which offers significant improvement in processing speeds
Moves both computation and state storage off chain
Derive security from Mainnet by publishing transaction results on-chain
Assume transactions are valid by default and only runs computation, via a fraud proof, in the act of a challenge
Thus, they don’t publish proofs of validity for transaction batches posted on-chain
After the rollup batch is submitted, it allows for a challenge period during which anyone can challenge the results of a transaction by computing a fraud proof
If the rollup batch remains unchallenged after the period elapses, it is deemed valid and accepted
Offers up to 10-100x improvements in scalability
Tech, Explained
Each optimistic rollup is managed by a set of smart contracts deployed on the network, which is where they will post transactions run off-chain in batches
On-chain contracts – the operation of the rollup is controlled by smart contracts, including contracts that store rollup blocks, monitor state updates on the rollup, and track user deposits
Off-chain virtual machine – where applications live and state changes are executed, serving as the upper layer (layer 2) for an optimistic rollup
Timeline of a transaction will look:
When users send transactions to off-chain Optimistic Rollups, aggregators sign up, and fraud proofs are committed
The aggregator deploys the transaction locally to generate a new smart contract, and after computing the new state root, the aggregator sends the transaction and state root back to the mainchain
If users believe that the aggregator has committed some sort of fraud in creating the root, they can challenge the aggregator by posting the correct state root and the proofs necessary to validate it
Once an invalid block has been identified and a fraud proof is complete, the L2 chain rolls back to resume at the previous non-fraudulent block
Challenges that these rollups face, despite allowing greater oversight, include (1) allowing the existence of an invalid blockchain state, which can exist until proof of fraud is submitted, (2) security issues, as they are vulnerable to attach due to their game theory based model, and (3) scalability, in the sense that optimistic rollups may require more mainchain computational resources as transactions scale → higher costs
Applications
L1/L2 interoperability – allows users to pass messages and arbitrary data between L1 and L2. also compatible with EVM such that users can post existing DApps to rollups or develop new DApps
Cross-chain contract calls – allows contract accounts on Ethereum to interact with L2 contracts using bridging contracts to relay messages and pass data between L1 and L2
Key Projects
Optimism – functions as a L2 scaling protocol for Eth applications, emulating the EVM experience to make it easier to build and deploy compatible applications. Supports existing Solidity smart contracts, off-chain wallet integrations, and user interfaces
Arbitrum – exists on top of the Eth blockchain and supports Ethereum remote procedure call interface (allowing compatibility with third party integrations), full EVM support, and Ethereum tooling (utilizes frontend Eth tooling such as Truffle, Hardhat, etc)
Boba Network – merges open-source OE tools with the research and development of OMG Foundation and Enya. designed to support DApps that are fast, low-cost, and very private
Read More
Boba Network’s Secure Multiparty Computation
Rollups – ZK Rollups
Executive Summary
Zero-knowledge rollups (zk-rollups) are a layer 2 scaling solution for blockchains
They aim to improve efficiency by moving computations and storage off-chain while keeping funds in smart contracts
Off-chain computation reduces the amount of data that needs to be included on the main blockchain, which makes transaction processing faster and more cost-effective
Transactions are processed off-chain in batches, and each batch is verified by a zero-knowledge proof that proves the validity of the transactions without revealing their contents
Zk-rollups are similar to optimistic rollups in that they rely on validity proofs for transaction verification, but they use zero-knowledge proofs instead of fraud proofs
Just needs to post a summary of all transactions rather than all transaction data on-chain
Tech, Explained
ZK-rollups use a validity proof to verify transactions as well as update the zk-state, maintained by smart contracts
Users in the rollup sign transactions and submit to L2 operators for processing and inclusion in the next batch to be verified and posted on-chain
Sometimes, operator is centralized entity (sequencer) who executes transactions, aggregates them, and submits to the main layer
Note that centralized sequences are currently considered design flaws, and many protocols are actively working on projects that would decentralize these sequencers
Sequencer would be the only entity who is allowed to produce L2 blocks and add rollup transactions
Proof of stake validator set may be used to rotate the operator role – prospective operators deposit funds in the rollup contract, with the size of each stake influencing the staker’s chances of getting selected to produce the next rollup batch
The ZK-rollup’s state, including L2 accounts / balances, is represented as a Merkle tree. A hash of the Merkle root is stored on-chain, which allows the rollup protocol to track changes in the state of the rollup.
After the execution of a new set of transactions, the rollup transitions to a new state
If the validity proof associated with the batch is verified by the contract, the new Merkle root becomes the rollup’s state root
ZK-rollups use validity proofs, a cryptographic technique that was covered in the first section, to verify the correctness of batched transactions such that the proposed state commitment can be accepted
Applications
Unlike optimistic rollups, ZK rollups are not readily compatible with the EVM, as proving general purpose EVM computation in circuits and more difficult and intensive than proving simple computations like the ones that ZKs use
Advances in ZK tech are igniting interest in wrapping EVM computation in zero knowledge proofs
Transaction data compression – ZK rollups help to extend the throughput on Mainnet by taking computation off-chain by compressing transaction related data to significantly increase the number of transactions processed per block
Reduce the costs of publishing calldata on Eth Mainnet and minimize rollup fees for users
ZK proofs can verify other proofs – recursive proofs heavily contribute to increasing throughput
Key Projects
Polygon zkEVM – L2 consensus mechanism for batching, verifying, and sending transactions to the Ethereum network
zkSync – used by dApps like Yearn Finance, FRAX, and Zerion. Working to increase Ethereum’s throughput while also preserving decentralization.
Scroll – zkEVM based rollup on Eth that enables native compatibility for existing Eth apps and tools
Developed a new hierarchical zk proof system, enables easy deployment of DApps on L2 and efficient verification
Able to establish efficient communication channels between DApps and their counterparts
Introduces L2 mining, which incentivizes miners to general zk proofs
Read More
Comparing zkSync and StarkWare
ZK-EVMs
Executive Summary
A zero-knowledge Ethereum Virtual Machine is a vm that executes smart contract transactions in a way that is compatible with both zero-knowledge proof computations and existing Eth infrastructure
Enables them to be a part of zk-rollups – they are a subset as they similarly allow smart contracts to be executed off chain using similar zero knowledge proofs
The original EVM wasn’t designed to work with zk-proof computations, so zkEVM is an attempt to build a EVM-compatible for rollups with zk-proofs while preserving EVM codes and the knowledge in it
A zkEVM replicates the Ethereum environment as a rollup, which brings the benefits of Ethereum and the existing tooling it employs to a more scalable and secure layer 2
Tech, Explained
The EVM executes smart contracts and computes the state of the Ethereum network after each new block is added to the chain along with its accompanying zero-knowledge proof
Type 1 zkEVM (fully Ethereum equivalent)
Doesn’t change any part of Ethereum system to make generating zk proofs easier, making them fully compatible with Ethereum-native applications and tools, which can be reused. Downside is that certain parts of the Ethereum protocol require a lot of computation to generate even zk proofs, so long proving times are involved
Key Project: zkEVM Community Edition – open source solution to validate Ethereum blocks via zk proofs, aiming to achieve 100% compatibility with EVM
Type 2 (fully EVM equivalent)
Aim to be fully compatible with existing Ethereum applications, while making minor modifications to make proof generation faster and development easier. Though proving time is faster, current implementations are still considered too slow
However, there is considered to be perfect equivalence at the VM level, as they make changes to data structures that hold the Ethereum state which the EVM cannot access directly
Key Projects: Scroll has enabled native compatibility for existing Eth apps and tools through creating a new hierarchical zero knowledge proof system
Type 2.5 – EVM Equivalent except for gas costs: here, we have increased gas costs while much more efficient proving times.
Type 3 (almost EVM equivalent)
Sacrifices EVM features to enable easier application development and proof generation (ie. changes to precompiles, VM memory, the stack, and how smart contract code is treated). Most applications on Eth will work in this environment but some may need rewriting
Key Project: Polygon Hermez
Type 4 (high level language equivalent)
Works by taking smart contract source code written in a high-level language and compiling that to some language that is explicitly ZK-SNARK friendly
Very fast prover times, but more incompatibility as contract addresses may change, and lots of debugging infrastructure cannot be carried over
Key Projects: ZKSync is working on adding bytecode compatibility , Nethermind’s Warp is working on compiling from Solidity to Sarkware
Applications
Secure scalability – since zkEVMs do not have to follow Ethereum’s consensus protocol rules, while still verifying all transactions, zkEVMs can optimize for speed and transaction throughout without compromising security
Lower costs – unlike other rollups that post batches of transaction data on-chain, zkEVMs only need to publish final state changes on-chain, since zero-knowledge proofs will guarantee the validity of all the transactions within a given batch
Faster finality time and network effects for developers and dApps
Read More
More on Nethermind’s Warp and how it will turn Starknet into a T4 system
Deep dive into the tech behind zkEVMs
Cool Twitter deep dive into Polygon and its tech
STARKS (StarkWare)
Executive Summary
StarkWare aims to solve the scalability and privacy problems of the blockchain, developing a complete solution that uses STARK technology to generate/verify proofs
Developed zk-STARKs to be more scalable and transparent, claims to be faster and more scalable than its competitors and other types of rollups (such as optimistic or zk-SNARKs)
zk-STARKs are a slightly newer model first used in 2018
These proofs focus on enhancing scalability, allowing developers to perform computations and store data off-chain, which significantly increases scalability
Used to verify these off-chain activities and are subsequently shared online for interested parties to confirm their validity
Combines proofs with a cryptographic hash function, which both contribute to scalability and transparency as it allows verifiers to rely on fewer but safer cryptographic assumptions
The implementation of transparency in STARKs largely differentiate them from SNARKs, meaning that they use publicly-available randomness to generate parameters, hence eliminating the need for a trust setup
STARKs are quantum resistant, but have larger proof sizes so it is slower
Uses hash functions, a storage saving tool, which are more resistant to collisions as part of their argument of knowledge computation
Since the parameters are public, this limits centralization and empowers transparency
Tech, Explained Behind Each Key Project
StarkNet – permissionless, decentralized, and censorship-resistant STARK ZK-Rollup, which will enable applications to scale without security compromises
Saves Ethereum from having to check and verify the validity of every single transaction on its chain, which is what often leads to network congestion
Helps to reach transaction speed of 100,000 TPS
StarkEx – StarkWare’s L2 scalability engine, which handles complex trading logic (ie. derivatives, spot trading, NFTs, and payments) using a STARK based Zk-Rollup. For projects integrating with StarkEx, there are minimal changes to be made while gas fees are dramatically reduced and no trust is required
Has an off-chain component which holds the order transaction executive, the state, and sends state updates. The on-chain component, in contract, enforces the validity of state transition and holds the state commitments and system assets
Since StarkEx is permissioned, StarkEx is permissioned and thus tailored to the needs of specific dApps
DApps can choose to roll up their data in (1) the ZK-rollup mode, (2) off-chain in Validium, or (3) Volition, a hybrid of 1 and 2
With rollups, ledgers are posted directly on the blockchain. However, since storing data on the blockchain is very gas intensive, the majority of the gas costs involved with this method go to data availability and not proof verification
Validium – only stores a hash on chain, as it uses a Data Availability Committee to secure the ledger, which solves the issue of it being very gas-intensive to store data on-chain. The majority of gas costs here would be attributed to data availability, and not proof verification. Instead, ledger information is stored off-chain.
The Data Availability Committee would be a quorum of independent members that oversee the correct state update and keep copies of processed data.
Also ensures confidentiality from people reading the blockchain, as under rollup mode, the balance of each account at the time that proofs are submitted is public domain.
Volition – data availability architecture that provides a hybrid model of Validium and Rollup, by keeping one ledger on-chain, and another ledger with a Data Availability Committee. Then, user can choose one of the other two modes to use for individual transactions (ie. when buying expensive NFTs, Rollup Mode is probably better to secure the data scored on-chain, but when buying a cheap NFT, Validium would be a much more cost-efficient option)
No matter which is used, the validity of transactions is guaranteed by the overlying STARK structure
Cairo – Turing complete language running under the hood of StarkNet that can be used to generate STARK proofs, used by developers to define any business logic and to send transactions to a Shared Provider Service when verifying logic off-chain.
Applications
NFTs – mass-minting is super gas intensive, so STARK scaling dramatically reduces the cost barriers
Perpetual Contracts Trading – since this type of trading needs to rely on frequent price feed updates for numerous asserts, this logic is not super viable on L1 but thrives on L2
See dYdX example below
Spot trading – removes downsides in liquidity, privacy, speed, and fees to help DeFi run at an unprecedented scale
DeFi Strategies – DeFi pooling
AMMs – Starkware provides dAMM, a design where liquidity can be shared by multiple L2 solutions
Data management, voting, payments, and more applications that are data-intensive and thus very costly or highly unsustainable for gas fees
StarkWare has also been used for the following applications:
DeversiFi: increasing transaction TPS to 9k, payment TPS 18k.
iMMUTABLE: decreasing cost of NFT minting gas to 0.2 cents, daily L2 transaction > weekly L1 transaction.
dYdX: Each transaction fee is reduced by 50 times.
Read More
More on StarkEx applications and their documentation
How Twitter has used StarkWare for account abstraction
High level breakdown of zk proofs used in StarkWare
DeFi
Lending/Borrowing
Executive Summary
DeFi lending/borrowing is a type of peer to peer lending operating on-chain without intermediaries
Lending protocols allow users to deposit funds and receive annual yields in return, or for borrowers to borrow tokens against deposited tokens as collateral
People use these applications as a way to borrow tokens to trade
Compared to traditional lending, DeFi is less time-consuming and has the ability to grant loans quicker as individuals only have to meet collateral requirements
Smart contracts take care of the reviewing process and offer accountability for proof of transactions
Technically more universally accessible, with no need for any level of KYC (no info needed)
The market’s annual percentage yields are oftentimes higher than the interest rates that traditional lending offers
Tech, Explained
In traditional finance, collateral is required that is associated with loans to validate the loan and verify that the borrower is trustworthy, while also creating incentive to not default on the loan
Same goes with DeFi, except with an anonymous system, there needs to be a different approach to putting down collateral for loans
To get a loan, the borrower needs to offer something more valuable than the loan amount (e.g. lock in $100 of ETH for $80 of UNI)
Collaterals are available in a wide range of variety: any crypto token can be use to exchange borrowed cryptocurrency
Many protocols are exploring the concept of undercollateralized loaning as well, making DeFi more accessible and increasing the amount of applications and use cases of the field
Smart contracts are used to deposit an amount of currency that has to have a value that is at least equal to the loan amount
Smart contracts take care of the entire process, allowing lending and borrowing activities to be conducted in a decentralized manner in which the parties involved in a transaction can deal directly with each other without an intermediary or a financial institution
They are self executing computer codes that use certain logics to carry out the rules of a transaction that are embedded in them
These rules and loan terms can include fixed interest rates, the loan amount, contract expiry date, etc
Automatically executed when certain conditions are met
Users will deposit their assets in a smart contract, and they become a lender!
Then, borrowers provide crypto assets in exchange for other crypto assets that they wish to borrow from one of the protocols
The overcollateralization involved in DeFi lending and borrowing is made to account for unexpected expenses and risks associated with decentralized financing
To gauge the performance of a protocol can be done through observing the total value locked on such platforms, which helps to measure the assets staked in smart contracts
The higher the TVL, the more secure the protocol is
Applications
Crypto wallets and lending protocols such as Metamask and Argent enable users to be the sole managers of their crypto assets, allowing users to interact with dApps securely
Undercollateralized lending
Some protocols, such as TruFi, Maple Finance, and Goldfinch, are working on protocols where users are able to borrow and lend without the high collateral requirements that are typically associated with DeFi borrowing
Typically used in applications of emerging markets and lending to people who have less access to crypto access and are trying to finance in the space
This normally comes with some form of KYC
Stablecoins – dollar digital currencies that enable investors to generate yield on their crypto assets in the DeFi market while alleviating the potential adverse effects of market volatility
For example, if an investor places ETH into the compound protocol to earn interest, there is a possibility that an ETH price drop will offset all yield earned
However, if the investor uses a stablecoin, such as USDC, the value of the underlying asset would remain stable so the yield would remain unaffected by market volatility
Investors looking for more yield than traditional fixed-interest investments — such as savings accounts, money market funds, or bonds — can digitize their funds to earn above-average yields in the DeFi market
Yield farming – placing crypto assets into DeFi protocols to generate the highest returns possible
Liquidity mining – providing liquidity to DeFi protocols in return to newly minted protocol tokens
Key Projects
AAVE – users deposit digital assets into liquidity pools, which become funds that the protocol can lend out
Launched GHO, a decentralized and collateralized stablecoin
Built atop ETH network, but has since expanded
MakerDAO – stablecoin on the ETH blockchain, keeps value as close to one US dollar as possible through system of smart contracts and decentralized participants
Goldfinch – working on undercollateralized lending in emerging markets
Read More
DeFi transforming lending routes on the blockchain
Decentralized Exchanges
Executive Summary
Decentralized exchanges (DEXs) are digital marketplaces for trading cryptocurrencies and other digital assets
Solidity developers created decentralized exchanges using AMMs in response to centralization
Further, they are peer-to-peer marketplaces where cryptocurrency traders make transactions directly without handing over management of their funds to an intermediary or custodian → decentralized
DEXs operate on decentralized blockchain networks, which eliminates the need for a central authority to oversee transactions
Links buyers and sellers of cryptocurrencies
Non-custodial, which means users keep control of their wallet’s private keys
Offer greater privacy and security compared to centralized exchanges since users retain control over their assets
Typically rely on automated market makers (AMMs) or order books to facilitate trades between buyers and sellers
AMMs use algorithms to set the price of assets based on supply and demand, while order books match buyers and sellers based on their desired prices
Rely on smart contracts to allow traders to execute orders without an intermediary
In contract, CEXs are managed by centralized organizations that are involved in financial services
Though these account for the vast majority of trading volume in the cryptocurrency market, because they are regulated entities, decentralized exchanges are getting more popular because they allow users to trade directly from their wallets
Tech, Explained
Built on top of blockchain networks that support smart contracts and where users can keep custody of their funds, so each trade will incur a transaction fee along with a trading fee
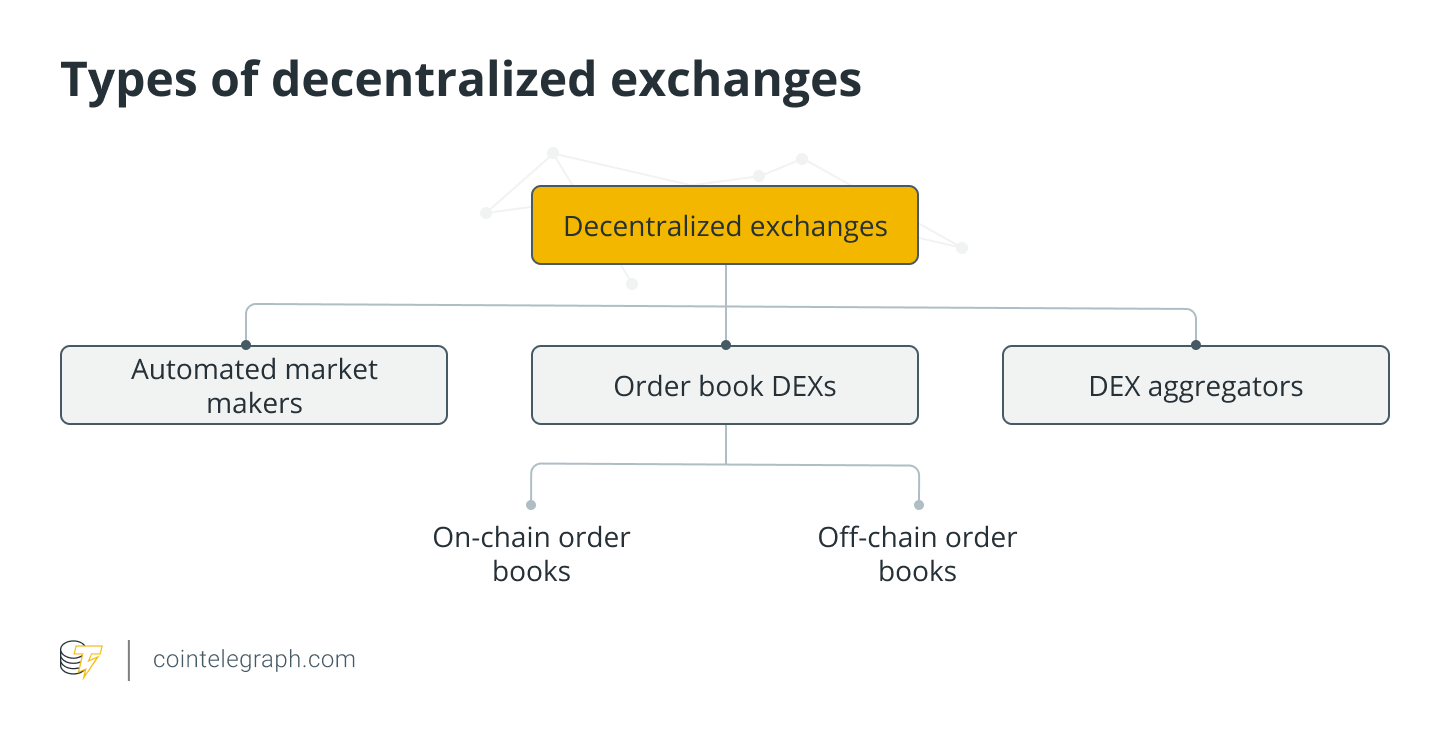
Three types of decentralized exchanges – all allow users to trade directly with each other
Automated market makers (AMMs) – a system that relies on smart contracts that was created to solve the liquidity problem
Rely on blockchain-based services that provide information from exchanges and other platforms to set the price of traded assets called blockchain oracles
Instead of matching buy orders and sell orders, the smart contracts of these decentralized exchanges use pre-funded pools of assets known as liquidity pools
The pools are funded by other users who are then entitled to the transaction fees that the protocol charges for executing trades on that pair
Liquidity providers need to deposit equivalent values of each assets in the trading pair in order to earn interest on their holdings – liquidity mining
If they attempt to deposit more of one asset than the other, the smart contract behind the pool invalidates the transaction
Using liquidity pools allows traders to execute orders or earn interest in a permissionless way
This model has a downside – slippage. Slippage is what occurs when a lack of liquidity on the platform results in the buyer paying above market prices on their order, with larger orders facing higher slippage
Lacking liquidity can deter wealthy traders from using these platforms
Liquidity providers also face risks including impermanent loss (direct result of depositing two assets for a specific trading pair). When one asset is more volatile than the other, trades on the exchange can lower the amount of one asset in the liquidity pool
Order books compile records of all open orders to buy and sell assets for specific asset pairs – buy orders signify that a trader is willing to buy or bid for an asset at a specific price, while sell orders indicate that a trader is ready to sell or ask for a particular price for the asset under consideration
The spread between these prices determines the depth of the order book and the market price on the exchange
DEXs using order books often have to hold open order information on chain (historically), while users’ funds remain in their wallets
Allow traders to leverage their positions using funds borrowed from lenders on their platform
Leveraged trading increases the earning potential of a trade, but increases the risk of liquidation
Enhances the size of the position with borrowed funds, which have to be repaid even if the traders lose their bet → liquidation
To offer leveraged trading options, these exchanges also allow users to lend their funds to other traders
Since they are essentially competing with centralized exchanges and incur extra fees because of what’s paid to transact on-chain, traders usually stick to centralized platforms
DEX aggregators use several different protocols and mechanisms to solve problems associated with liquidity – these platforms aggregate liquidity from several DEXs in order to minimize the slippage associated with large orders, optimize swap fees, token prices, and offer traders the best price possible in the shortest possible time
Protecting users from the pricing effect and decreasing the likelihood of failed transactions are other goals of DEX aggregators
Some will also use liquidity from centralized platforms in order to provide users with a better experience
Still remain non-custodial by leveraging an integration
Applications
Token availability – Centralized exchanges have to individually vet tokens and ensure they comply with local regulations before listing them, but decentralized exchanges can include any token minted on the blockchain they are built on, which means that new projects will likely list on these exchanges before becoming available to centralized options
Trustless transactions – through smart contracts, DEXs execute trades and record them to the blockchain, making them less likely to be targeted by hackers
Privacy – traders that are using DEXs don’t need to disclose their private keys because wallets are held externally and the DEX is not liable for the funds
Key Projects
Uniswap
Built on top of the ETHh blockchain, which makes it compatible with all ERC-20 tokens and infrastructure such as wallet services
Completely open source, which means that the code is open to anyone to view
Allows users to list tokens on the exchange for free
dYdX
Built on ETH L2 StarkWare, utilizing StarkWare’s ZK proofs to create more secure and decentralized platform
Designed to support the trading of perpetuals, which are a derivative that derives value from an underlying asset
Uses an order book
Curve Finance
ApolloX
1inch - most popular DEX aggregator
Read More
More on DEX from investor perspective
Pools and LP Positions
Executive Summary
A liquidity pool is essentially a group of tokens or assets locked into a smart contract to enable decentralized token swaps, lending, borrowing, and other activities on-chain
Each liquidity pool will have a specific composition of assets (usually 2-3 specific tokens) where the amount of Token A + Token B = 'LP AB', and liquidity providers must deposit equal proportions (in market value) of each token to enter the pool
Form the backbone of decentralized exchanges
Some DEXs do not use an order book to create the market price – automated market makers (AMMs) govern the liquidity pools in DeFi, and algorithmically balance the pools to determine the price
The more assets in a pool and the more liquidity the pool has, the easier trading becomes on decentralized exchanges
Liquidity pools aim to solve the problem of illiquid markets by incentivizing users themselves to provide crypto liquidity for a share of trading fees
users can simply exchange their tokens and assets using liquidity that is provided by users and transacted through smart contracts
Tech, Explained
An operational crypto liquidity pool must be designed in a way that incentivizes crypto liquidity providers to stake their assets in a pool
Liquidity providers earn trading fees and crypto rewards from the exchanges upon which they pool tokens
When a user supplies a pool with liquidity, the provider is rewarded with liquidity provider tokens
Some protocols will offer even more incentives for users to provide liquidity by providing more tokens for particular incentivized pools
Take an example for how incentivization works:
Say a trader wants to invest 20k in a BTC-USDT liquidity pool using SushiSwap
They would deposit a 50/50 split of BTC and USDT to the liquidity pool
They would then receive liquidity provider tokens from the BTC-USDT pool
Then, they would deposit LPTs to the staking pool, and receive the SUSHI token as a reward after the lockup period that they agreed to hold within a vault
AMMs allow for on-chaint reading without the need for an order book with liquidity pools
When you are executing a trade on an AMM, there is no counterparty – instead, the trade is executed against the liquidity in the pool
For the buyer to buy, there doesn’t need to be a seller at that particular moment, only sufficient liquidity in the pool
Impermanent loss refers to a phenomenon that can occur when providing liquidity to an AMM
As has been discussed, depositing an equal value of two assets into a liquidity pool makes it such that the price of each asset in the pool is determined by the ratio of the total value of each asset in the pool. So when a user swaps one asset for another on the AMM, the price of the assets in the pool shifts which will cause the ratio of the assets to change
If the price of one of the assets in the pool changes significantly relative to the other asset, the liquidity provider may experience impermanent loss
This occurs because the value of the assets they deposited has changed while they were providing liquidity, and when they withdraw their assets from the pool, they may receive fewer assets than they originally deposited
The loss is called "impermanent" because it only occurs if the price of the assets changes and is temporary because the price of the assets can change back to their original value
See resources section for additional information on impermanent loss as a risk for investors
Applications
Early stage DEXs suffered from liquidity problems when attempting to model a system of finance after traditional market makers
Liquidity pools helped address this problem by having users be incentivized to provide liquidity instead of having a seller and buyer match in an order book
Yield farming is the practice of staking cryptocurrencies within a specific protocol to generate tokenized awards
Allows exchange liquidity providers to collect high returns for slightly higher risk as their funds are distributed to trading pairs and incentivized pools with the highest trading fee and LP token payouts across multiple platforms
Blockchain based online games
Tranching – dividing up financial products based on their risks and returns
Allow LPs to select customized risk and return profiles
Minting synthetic assets on the blockchain also relies on liquidity pools
Users can add collateral to an LP, connect it to a trusted oracle, and create synthetic tokens that are pegged to whatever assets they want to connect it to
Key Projects
SushiSwap - anyone can provide liquidity to their liquidity pools, and when they do, they will receive SLP tokens
Tokens represent a proportional share of the pooled assets, allowing users to reclaim their funds at any point
Value of the SLP tokens is updated with each trade to add their value relative to the tokens the pool uses to trade
Uniswap
Curve - decentralized liquidity pool for stablecoins based on the Ethereum network. It provides reduced slippage because stablecoins aren't volatile
Balancer – decentralized platform providing a few pooling options such as private and shared liquidity pools offering catered benefits for its liquidity providers
Read More
Understanding liquidity pools as part of DeFi
Generating crypto income with liquidity pools
Understanding impermanent loss and how to avoid it
Layer One Interoperable Ecosystems
Polkadot
Executive Summary
For a system that is becoming increasingly adopted globally and digitalized, individual blockchains must be able to communicate with each other to ensure the large scale acceptance of blockchain based applications
Interoperability refers to the ability of disparate ecosystems to seamlessly exchange data and transfer relevant information between each other sans any centralized entity/intermediary
Essential to alleviating the roadblocks that are the bottleneck of further blockchain adoption at the moment
Polkadot is a Layer 0 multichain protocol that came into existence to address the low latency and scalability issues crippling Ethereum
Another option is bridging, as previously mentioned
Polkadot connects application specific Layer 1 blockchains (parachains) into one unified network via the Relay Chain
Relay Chain is responsible for security, consensus, and cross-chain interoperability across the entire network
Despite technical differences between public, permissionless networks, private consortium chains, and other Web3 technologies, Polkadot enables an internet that provides seamless communication and transfer of value between networks with security guarantees
Tech, Explained
The network runs on a sharded model that allows multiple blockchains to run in parallel, connected via the Relay Chain
The Relay Chain allows Polkadot to process transactions from all chains in the network at the same time
Eliminates the bottlenecks of legacy networks (refers to traditional centralized networks that can only process one transaction at a time), also improving scalability
This simultaneous transaction processing is referred to as parallel processing → blockchains on Polkadot are called parachains!
Parachains are sovereign blockchains offering specific use cases and featuring their own tokens and governance systems
For a parachain to be compatible and usable on Polkadot, they just have to have logic that can compile to WebAssembly and adhere to the Relay Chain
WebAssembly is a binary instruction format for a stack based VM, designed to be a portable target for the compilation of high level languages, which enables deployment on the web for client and server applications
There are only 100 parachains allowed on the network, and these parachains are sold/granted through an auction system
Substrate is the technology that is underlying in the Polkadot ecosystem – it is a blockchain SDK framework
All chains made with the toolkit are compatible with Polkadot, and will gain access to its speed, security, and interoperability
Optional for building on Polkadot, as the two are not dependent on each other
Substrate allows you to create specialized blockchains for any use case, and was used by Parity Technologies to create Polkadot itself
While Substrate can be used to build any type of blockchain, not just Polkadot parachains, connecting to Polkadot offers a multitude of benefits
Substrate-based chains are easy to integrate into Polkadot or Kusama to become a parachain or parathread
The Relay Chain forms the basis of the ecosystem
It is responsible for securing, governing, connecting, and ensuring the seamless functioning of parachains
Does not support application functionality, but its primary purpose is to validate the state transition of all connected chains and providing a shared state “State of States” across the entire network
Parachains connected to the RElay Chain can execute smart contracts and support dApps, besides creating and transferring assets on the network
Relay Chain is what allows Polkadot to ensure security, which is paramount as a concern when it comes to transferring data between parachains
The Polkadot wallets, accounts, and governance are all structured in the Relay Chain framework
Parachains are then Substrate-based blockchains that connect to available slots on the Polkadot platform
Collators facilitate the different parachains transactions by maintaining a full-node of the parachain blockchain and the Relay Chain
Must be incentivized by the individual parachain in order to be rewarded for the service provided to them
Rewarded via token or transaction fees
Polkadot system has no set rules on how collators are incentivized to work with the parachains and it’s up to the parachains to provide an economic incentive to attract enough collators to their blockchain
Nominated Proof of Stake (NPoS) is the consensus mechanism used to create and validate blocks in the Polkadot blockchain
Blockchains that are not built on the Substrate framework use specialized bridge contracts or modules to connect to Polkadot
Applications
Polkadot’s cross-chain messaging scheme (XCM) facilitates the exchange of data, allowing for true interoperability and creating a new paradigm of interchain services, communities, and economies
Enhanced scalability for Layer 2 solutions
Parachains are free to configure the consensus model that affects its own blockchain security and speed allowing them to scale more easily since they are just an interoperable independent chain
Developers can leverage and build on features/offerings of multiple blockchains rather than being restricted to the features of a single blockchain
XCMP (Cross Chain Message Passing) is the common framework used in Substrate based blockchains to communicate, which enables smart contracts in each individual chain to understand a standard logic for representing the unique assets and messages
The Polkadot Substrate framework gives blockchain researchers a new framework to test concepts and applications, which is super relevant in blockchain research
Read More
The UX of Interoperability: XCMP vs IBC
Elements of Polkadot explained, roles involved in staking explained
Polkadot compared with Cosmos and Avalanche
Cosmos
Executive Summary
Dubbed the Internet of blockchains, Cosmos was built to facilitate communication between standalone distributed ledgers without the need for centralized intermediaries, which we have already covered as the main need for interoperability in blockchain scaling solutions
Cosmos’ approach is different from the interoperability solutions that involve the use of smart contracts
Instead, it offers open-source tools for developing independent blockchains referred to as zones
The zones connect to the main blockchain, and communicate with the blockchain through the use of the inter-blockchain communication protocol, which will be covered below
Unlike Polkadot, validators on Cosmos are independent
Also does not have one central hub like the Relay Chain, but rather several
Zones connected to the Cosmos Hub do not have uniform security – they maintain their own validators and use IBC to facilitate the transfer of data to other zones by routing through the hub
Cosmos interoperability extends to blockchains that do not have fast-finality
This includes proof-of-work blockchains, such as Bitcoin
Designed to generate thousands of interconnecting blockchain systems, the Cosmos Hub is a proof-of-stake platform where participants stake their ATOM coins to earn rewards
Tech, Explained
Hubs and Zones
The protocol is used to connect separate chains (Zones) to a special blockchain (Hub)
Once a Zone is connected to the Hub, it can communicate to every other chain connected to that hub
This is where Cosmos is similar to Polkadot, except there are many options for Hubs rather than just one
Each zone can function autonomously, from authenticating accounts and transactions to creating and distributing new tokens and executing blockchain changes
Different zones built on Cosmos can have vastly different applications to achieve their goals, just need to fulfill the requirements of being compatible with IBC
Inter-Blockchain Communication Protocol – A system that allows different blockchains to connect and communicate with each other
Enables the exchange of information between blockchains in the Cosmos ecosystem
Designed to work with a wide variety of blockchains – in order to be IBC compatible, blockchains just need to have consensus layers with instant or fast finality
This typically just excludes proof of work blockchains
However, allows interoperability with proof of work blockchains through bridges, even if they don’t specifically meet the requirements of the Cosmos protocol
Ideal for connecting Tindermint chains into one cohesive ecosystem
Can also facilitate communication with external chains that also have fast finality
Cosmos blockchains can practically do anything they want using IBC from crypto to nonfungible token (NFT) transfers, as well as cross-chain smart contracts
Tendermint Byzantine Fault Tolerance Engine – consensus protocol that allows developers to create a proof-of-stake blockchain that is fast, scalable, secure
Used by default by the Cosmos SDK tools to secure the network
Allows developers to build blockchains without coding from scratch
Validates transactions and executes blocks to the blockchain
Uses the application blockchain interface to connect to applications
Functions through a proof of stake governance mechanism that supports integrating the computers’ distributed network running Cosmos Hub
Cosmos Software Development kit – Cosmos seeks to make building on top of Tindermint as easy as possible, using SDK to do this
Generalized framework that comes with robust tools for developing secure apps on Tindermint
Has a modular design, which allows a lot of flexibility to developers
Peg Zone
Mechanism employed by the Cosmos ecosystem to allow blockchain protocols (which can lack settlement finality) to interoperate with the Cosmos network
Normally, they would use the IBC protocol
However, it can only be used correctly if both the starting and ending chains are able to achieve settlement finality
To solve this, peg zones were built to serve as a translator zone or “finality gadget”
Generally employ a 2-way peg, which means that assets can be sent bidirectionally between the chains
Participants in the network can stake ATOM and earn rewards – the top 100 stakers can become validator nodes to power the blockchain and vote on changes
The higher the amount of ATOM staked, the higher the voting power of the validators
Users can also choose to delegate their tokens to validators and interchange them, which incentivizes validators to perform honestly
Applications and Mental Model
Cosmos’ objective is to enable communication between all blockchains while solving the three main problems: sovereignty, scalability, and sustainability
Sovereignty – The Cosmos free SDK allows developers to build sovereign blockchain apps without ongoing costs. Though Cosmos, these blockchains can easily interconnect without relying on smart contracts
Avoids high transaction costs due to network congestion
Better scaling features as a parallel effect!
This will help to boost functionalities in DeFi, NFTs, gaming, DAOs, social networks, etc
Scalability – Cosmos interoperability is what guarantees the functioning of a scalable system
By integrating to Cosmos interoperability model of shared communication standards, any type of sovereign blockchain will be able to communicate with each other and contribute to the evolution of its protocol design
Sustainability – assured by the proof of stake consensus algorithm, which secures the network
Helps to reduce carbon footprint compared with proof of work
Comparing Cosmos and Polkadot
Cosmos and Polkadot are competitors doing similar things towards the same goal –
Cosmos’ tech is arguably simpler and they have created a platform on which it is easier to build on
They have somewhat of a head start
Polkadot is the turtle in this race
Read More
More on the tech behind peg zones
Interoperability via peg zones
More comparing cosmos and polkadot that is also interesting
Interoperability – top three protocols and their comparisons
Oracles
Executive Summary
Oracles are entities that connect blockchains to external systems, enabling smart contacts to execute based upon inputs and outputs from the real world
Oracles provide a way for the decentralized Web3 ecosystem to access existing data sources, legacy systems, and computations
The blockchain oracle problem refers to a fundamental limitation of smart contracts – the issue is that they cannot inherently interact with data and outside systems that are disconnected from their native blockchain environment
This isolation from external systems allows blockchains to obtain their most valuable properties, but the vast majority of smart contract use cases do require knowledge of real world data and off chain events
Decentralized oracle networks (DONs) allow for the development of hybrid smart contracts that combine on-chain code with off-chain infrastructure
These hybrid smart contracts enable advanced decentralized applications (dApps) that can respond to real-world events and interact with traditional systems
DONs act as a bridge between the blockchain and the outside world by providing reliable and tamper-proof data to dApps
This access to real-world data allows dApps to respond to external events, making them more powerful and flexible than purely on-chain applications
Hybrid smart contracts also allow dApps to interact with traditional systems, such as legacy databases or payment systems, making them more versatile and interoperable
Tech, Explained
Given the extensive range of off chain resources, there are many different types of oracles that have all sorts of different applications in delivery and levels of security
Generally, each oracle has a different approach to fetching, validating, computing upon, and delivering data to a destination
Input oracles - fetches data from the real-world (off-chain) and delivers it onto a blockchain network for smart contract consumption
These provide DeFi smart contracts with on-chain access to financial market data
Output oracles - allow smart contracts to send commands to off-chain systems that trigger them to execute certain actions
Can include informing a banking network to make a payment, IoT systems, etc
Cross-chain oracles - can read and write information between different blockchains
Enable interoperability, as they can move both data and assets between blockchains
Compute-enabled oracles - newer variant of oracle that is becoming more popular, as they use secure off-chain computation to provide decentralized services that are impractical to do on-chain due to technical, legal, or financial constraints
Can computer zero-knowledge proofs to generate data privacy, run verifiable randomness functions, etc
Oracles can retrieve data from various sources, including APIs, websites, and sensors, and then provide this data to the smart contract to trigger the appropriate actions
Applications
Oracles play a critical role in enabling a range of blockchain use cases such as
DeFi
A large portion of the ecosystem requires oracles to access financial data about assets and markets
Ie. some decentralized money markets will use price oracles to determine borrowing capacity and check undercollateralized positions
Synthetic asset platforms use price oracles to peg the value of tokens to real world assets
Supply chain management
Enterprise
Cross-chain oracles can be used to connect backend systems of enterprises to any blockchain network
This allows these systems to read/write to any blockchain and use complex logic to deploy assets and data across chains
Prediction markets
Sustainability
Hybrid contracts are advancing sustainability by creating better incentives to participate in greener, healthier practices through advanced verification techniques
Insurance
use input oracles to verify the occurrence of insurable events during claims processing, opening up access to physical sensors, web APIs, satellite imagery, and legal data
Challenges and risks – despite the overwhelming potential of oracles and their role in furthering the innovation of blockchain technology, there are certain obstacles that need to be addressed in order to ensure the security and integrity of the blockchain ecosystem
Potential data inaccuracies
Data breaches
Regulatory compliance issues
Key Projects
Chainlink – aims to overcome the oracle problem by using decentralized oracles to prevent data manipulation, inaccuracy, and downtime.
Developed a decentralized oracle network to combine multiple independent oracle node operators and reliable data sources to establish end to end decentralization
Incorporates three layers of decentralization to eliminate any single point of failure
Working on data feeds (decentralized data feeds for DeFi, reserves, NFTs, etc), Chainlink functions (connecting smart contracts to a trust-minimized compute infrastructure), automated contracts (decentralized, reliable, and cost-efficient automation for smart contracts), VRF v2 (tamper proof RNG for blockchain gaming and NFTs), external API calls (requesting and receiving data from any API using a contact library)